Researchers hack Telegram accounts through SS7 protocol
SS7 VULNERABILITY
White Hackers from Positive Technologies shown how to exploit SS7 protocol to login into Telegram accounts by intercepting SMS messages.
A few days ago we read that someone detected security problems in these applications, but due to an external agent (this is not Telegram’s fault), something we know as Signaling System 7 (SS7), a global network of carriers that acts as a central hub to connect the world.
As said, these two hacks aren’t attacking the encryption in the app(s), however, they’re attacking the SS7 vulnerability. This is done by tricking the telecom network into believing the attacker’s phone has the same number as the target’s. From there, the attacker would create a new WhatsApp or Telegram account and receive the secret code that authenticates their phone as the legitimate account holder.
As a result, the hacker now controls the account, so all your messenger activity will be under attacker’s control, being able to read/send messages as an original account holder.
SS7 VULNERABILITIES ARE NOT NEW
SS7 protocol flaws are known since 2014. The Signaling System No. 7 (SS7) protocol is a standard developed in 1975 that allows telco operators to interconnect fixed line and/or mobile telephone networks. The protocol is of great importance to the telephony communications backbone but was never updated to take into account the advancements made in current mobile technologies and remained grossly outdated.
Many security experts have warned about its lack of proper security measures ever since 2014. Infamous are two talks given by researchers at the 31st Chaos Communication Congress in Germany. Positive Technologies was also one of those companies, releasing an in-depth report about the protocol’s issues in December 2014.
TELEGRAM SOLUTION
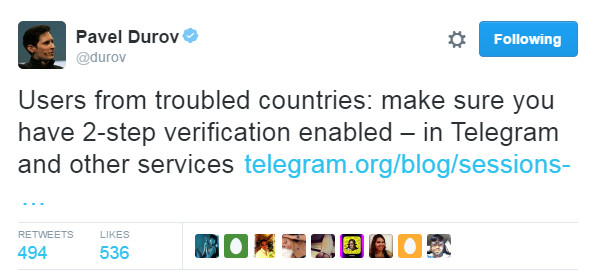
As Pavel Durov warned weeks ago, Telegram users should set the Two Step Verification. It allows you to set up a password that will be required every time you log into your account from a new device – in addition to the code you get in the SMS.
Learn more about SS7 attacks
- SS7 Attacks and Potential Breaches in Telecommunication Leading to Chaos.The Ukraine case.
- Worldwide attacks on SS7/SIGTRAN network
- The Fall of SS7
- SIGNALING SYSTEM 7 (SS7). SECURITY REPORT
Sources:

Follow us on Telegram Geeks Channel.





















“0$7#” this is shit “9$33@*”
show us how to hack telegram channels step by step, will appreciate
i educate hack of telegram: follow me on my telegram: +1 8109415353
O need know this process. Simeone teach me?