Filtered blocking code from WhatsApp

Someone commented on the blog some regular expression that was being used to block telegram on whatsapp’s APP:
“(\\W|\\b)telegram(\\.\\w+){1,2}\\z”.
So we wanted to probe that the blocking was not caused by a random glitch and there was an specific purpose of blocking Telegram links.
Firstly we downloaded the android APK directly from WhatsApp site: https://www.cdn.whatsapp.net/android/2.12.370/WhatsApp.apk
The code
The first surprise we noticed was that the apk is not obfuscated at all. So we used jadx to decompile it, and this is the result:
[Result of decompiling WhatsApp Version 2.12.370 (sha1: bf9c222b1acaa007d5e78a17ceace2bdd4d7d198) using jadx 0.6.0]
In the class LinkifyWeb.java we found the infamous regular expression: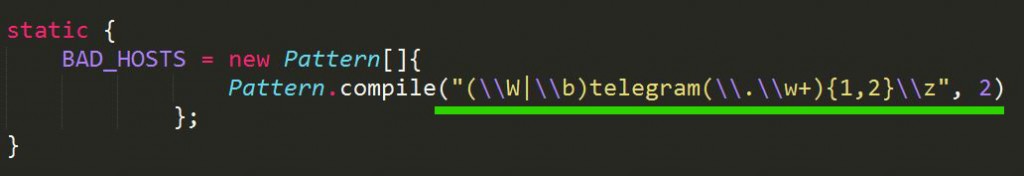
This regular expression means: Look for “telegram” string not preceded by anything, or preceded by a word separator, or preceded by non-word-character, then followed by some kind of domain TLD.
And this is the code that calls the regular expression and blocks any telegram URL at Whatsapp APP:
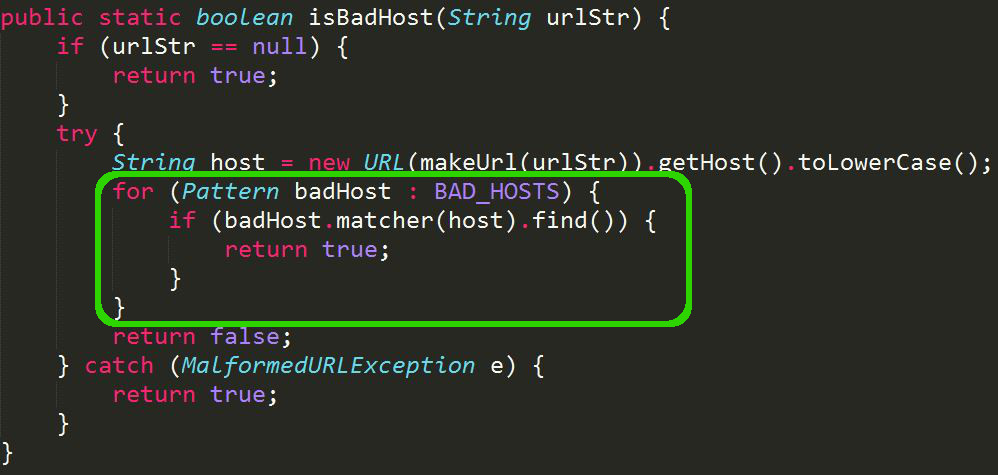
Every time someone sends an URL, this function analize it to see if the URL is a “badHost”.
So, this confirms that the blocking of telegram is not unintentional. It is crystal clear that WhatsApp targets Telegram and only Telegram specifically.
Bonus track: In their paranoia, whatsapp also blocked the domain telegram.com. That is not related with telegram.

Follow us on Telegram Geeks Channel.





















On top of doing abusive practices, they are bad coders.
[\W\b]telegram(?:\.\w+){1,2}\z
is almost twice faster.
I’m so bad with regex, but how not to trust someone with your name 😛
Twice faster for something that’s called very sporadically. Not really worth it and in particular NOT a good measure of their value as coders.
Tooop